New and improved
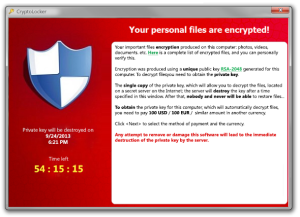
While the original version of Cryptolocker demanded 100 dollars to decrypt the files, the new version is asking for 300 dollars. It’s obvious that those controlling it realized they could make a lot more out of their criminal endeavor. Limited options IT security companies are struggling to undo the damage, but many are finding that paying the ransom is the only way out. Surprisingly, some of those that have paid the ransom report that in fact they were able to decrypt their locked files. On the other hand, some people have reported that despite paying the ransom they were not able to get a key or that it was not working for them which doubles their loss. As such, while you may not want to give in to the criminals, lacking proper and uninfected backup will leave you with no option, unless you are willing to lose all the affected files. Even when the files are successfully decrypted, the potential for reinfection exists, which is why it is best to reformat and start afresh once you get the files restored. Researchers from different antivirus vendors are working day and night to undo the damage, but as expected, this is proving very difficult. In order to decrypt the file, they require access to both the public and private keys that were used to encrypt them. What you can you do When dealing with Cryptolocker, prevention is definitely better than cure. The two main infection methods that have been identified are email attachments and botnets. The first line of defense for ransomware like Cryptolocker is YOU! Infections can easily be avoided by being careful with email attachments you were not expecting or from people you don’t know well and downloading files from questionable websites. If you can spot an obvious malware attack, you can prevent it from getting on to your computer. Also, make sure you have anti-virus software like ESET and be sure it’s updated. If you need anti-virus software to protect your computer against malware like Cryptolocker and other dangerous computer viruses, contact us. They should be equipped with the latest and greatest in computer and network security. Lastly, implement some kind of local and off-site (online) backup. Having both a local and off-site backup saves time, energy, and cost if you do end up getting a computer infection. The best prevention is to make sure your computer is up to date and free of malware by installing and running the latest version of your anti-virus and anti-spyware. Finally, regularly back up your files and store them in a safe location, preferably offsite. This will give you a good chance of recovering your files without too much trouble. If you are backing up with an external hard drive, first insure you are backing up (many people think they are, but are not) and eject the external hard drive from the computer in between backups. Do not risk the external hard drive getting encrypted. If you’re in need of immediate attention regarding the Cryptolocker virus or any other malware infection, give us a call. We provide computer repair and virus removal in Racine & Kenosha, WI and nationwide with remote technical support. We’ve personally resolved this and many other computer infections saving our customers the heartache of lost data. |
Tech Force BlogWe provide you with important, practical tips and insight for your technology and networks for both home and business. Archives
March 2024
Categories
All
|
Get in touch with us! |
See what our clients have to say...
Very pleased with Tech Force! We've been using Tech Force for over four years now. We've had a lot of different people do computer and IT stuff for us, but Tech Force is the first to come in and implement a plan. The plan was executed and we've had no problems. |
More Client Reviews
Read Our Customer Reviews |
We service Racine, Mount Pleasant, Sturtevant, Wind Point, Union Grove, Elmwood Park, Franksville, Caledonia, Kenosha, Somers, Pleasant Prairie, Bristol, Parkside, Oak Creek and Franklin, WI and surrounding areas. Copyright © 2009-2024 Tech Force Computer Service, LLC.

 RSS Feed
RSS Feed
