|
Remember the awe you felt when you turned on your new computer and it loaded in a flash? Your computer was the envy of your friends and you weren’t afraid to bathe in that glory. Button on, ready to go, those were the days! After a year or two though, it doesn’t seem to be quite as zippy…no, you’re not imagining it. It really has slowed down, not just in comparison to newer models and your expectations…There’s a measurable drop in speed and power that has nothing to do with worn out parts. The good news is a little maintenance can have that baby cruising at top speed again. Let’s take a leisurely walk through the system and spot the culprits: Start-up applications: It’s super convenient to have Skype start automatically and your anti-virus too. In fact, many of the applications starting themselves with the computer are essential to your experience. But some of them are getting a little too ‘helpful’.
For example, iTunes helper loads in the background to speed things up when you connect your device – but if you can’t even remember the last time you ran iTunes on your computer, then it can go. Programs like that are holding onto a portion of your processing power and adding to your speed issues. The average home computer automatically loads around 75 programs at start-up! Temporary junk: Computers are kind of messy. They leave temporary files and snippets of information all over your hard drive, each action leaving a trail rather like a roaming toddler with a sticky sandwich. Every webpage, every image on that webpage, every program you run and every game you play leaves something behind. It may be the tidbits of information called “cookies”, saved game files, auto-restore files or even a log so that you can hit the undo button 100 times while it remembers your actions for you. The more junk your computer builds up, the slower it gets. Viruses and malware: These infections sit in the background consuming resources while doing various nightmarish things. They may be spying on your actions, stealing your information or reaching out through your network to infect others. Occasionally, the impact is limited to seeing your computer slow to a crawl, however the flow-on financial costs of an infection can easily reach into the thousands. Bloating: With every new version of software comes a new set of features, introductory sequences and design improvements. The problem with this is the application becomes larger and larger with each new version, requiring more system resources to install and run – and slowing your computer down. Just like a car, computers need regular maintenance - we offer a Tune-Up service to bring your computer back to its original speed and extend its life. Give us a call at 262-515-9499 to book in a Tune Up. The message is clear: email is king. Many clients and customers choose to communicate primarily by email and as you know, it gives a fantastic ROI in your marketing strategy…unless you’re using a free email like Hotmail, Gmail, or even your internet provider. If that’s the case, you’re losing business each and every day. It looks unprofessional: Imagine if banks used free email accounts – you’d never feel comfortable giving them your personal details let alone any money. How people perceive your business is what makes your business. Without that professional touch, you’ll appear temporary and fly-by-night. It puts your credibility into question and sends the message that you’re not serious about doing business – or worse – that you’re prepared to cut corners.
It erases your experience: Newer, fledgling businesses often start out with a free email address. The address clearly communicates that they are new and have little experience, and are perhaps testing the waters in a new direction. They’re not even remotely proven yet and are firmly within the hobby-zone. Continuing to use the free address once your business moves into the professional arena means you’ll struggle to build momentum and any experience will be negated. It’s forgettable or inappropriate: Your business success hinges on being memorable enough to gain referral custom and results from your advertising. Unfortunately, free email addresses are by default filled with hard to remember clutter, for example – [email protected] or [email protected]. Neither of these roll off the tongue, is appropriate for business, or can be remembered without a high likelihood of typos and bounce back. Branded email addresses such as [email protected] make running a profitable, scalable business much easier. It’s not permanent or safe: When you use a free email address you are at the mercy of the email provider. They may close down operations or cancel your account for any reason. These types of accounts are also often hacked and leaked on a global scale. When a better internet or email deal comes along, you’re still stuck using the old address because it’s printed on your business cards, car lettering and flyers. Some will agree to keep the address open for a fee, but you’ll lose the control and flexibility you need to grow your business. With your own domain name, you own it and can move it to a new business-grade email service easily. You’ll also have complete master control over the addresses within your domain, resetting passwords and creating/closing accounts at will. Every employee shares one inescapable flaw that is putting your business at risk. They’re human. 59% of data breaches can be traced back to something an employee did (or didn’t do), which invited a cyber-attack. To lock hackers out, build security awareness and respect into your company culture, so that maintaining digital security becomes as routine as making coffee.
Starter Topics:
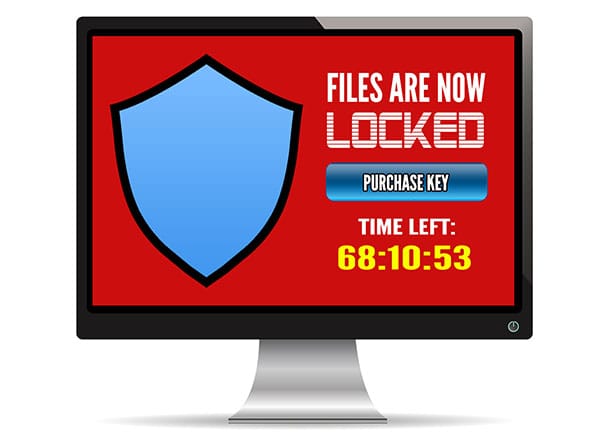
If you need help implementing better security practices in your business, contact us here. Ransomware has undeniably been the biggest security threat of 2016. No-one was safe. Hackers targeted everyone and everything, including home PCs – and they were astoundingly successful – earning themselves upwards of $846 million from US reported incidents alone. Business is booming for hackers, with thousands of attacks each day bringing in an average of $640 per target. Perhaps even more alarmingly, the financial cost of each individual attack is on the rise – the more ransomware proves to be an easy earner for them, the more they demand each time. For a quick payday, some hackers offer to ‘rescue’ you from immediate danger – for a fee. One method is to trick you into thinking you have a virus that will spread if you don’t pay money to remove it immediately. Another much scarier method is to pretend to be the FBI and say your computer was involved in a crime (anything from money laundering to child pornography) and you can avoid going to prison by paying a few hundred dollars.
Thousands of regular people are also waking up every day to discover they’ve been locked out of their own files. Entire music and video libraries, digital photos from the past 5 years, personal budget files and even their secret novel draft …all held hostage until the user pays a ransom. The encryption is so strong and unbreakable that paying the ransom often becomes the only solution. The way ransomware gets onto your computer is deviously simple. Generally, the hackers convince you to click an email attachment/link or pop-up. With both approaches, the hacker usually offers helpful information, for example:
It’s so tempting to click through for more details and that’s what the hackers count on. Their messages and pop-ups aren’t obvious threats and so slip easily under our radar. Unfortunately, they’re not the most trustworthy bunch so paying may not actually unlock your files, and one payment can quickly become several. To make matters worse, they can encrypt any backups connected to your computer too, like a USB drive. Having a backup is super important in any situation, but in cases like this, the right backup is needed. Not only one stored separate from your network, but one created recently with all the files you can’t bear to lose. Before restoring your backup, however, you’ll need to make sure the malware isn’t lurking in the background, ready to not just re-infect your restored files but also the backup drive itself. To avoid finding yourself up to the waist in ransom demands or sending hackers money each month, we recommend being wary of email attachments, even from friends and family. If you’re not sure what the file is, don’t click it. They may not have sent that email intentionally; their infected system may be auto-emailing everyone in the address book. You should also be careful with any popups that appear out of place, especially ones that try to make you panic. If it doesn’t sound right or look right, don’t click it. Ransomware is just too dangerous to risk. Contact Us to set your computer up with protections against ransomware, and put backups in place that will keep your important files safe. |
Tech Force BlogWe provide you with important, practical tips and insight for your technology and networks for both home and business. Archives
March 2024
Categories
All
|
Get in touch with us! |
See what our clients have to say...
Very pleased with Tech Force! We've been using Tech Force for over four years now. We've had a lot of different people do computer and IT stuff for us, but Tech Force is the first to come in and implement a plan. The plan was executed and we've had no problems. |
More Client Reviews
Read Our Customer Reviews |
We service Racine, Mount Pleasant, Sturtevant, Wind Point, Union Grove, Elmwood Park, Franksville, Caledonia, Kenosha, Somers, Pleasant Prairie, Bristol, Parkside, Oak Creek and Franklin, WI and surrounding areas. Copyright © 2009-2024 Tech Force Computer Service, LLC.



 RSS Feed
RSS Feed
