|
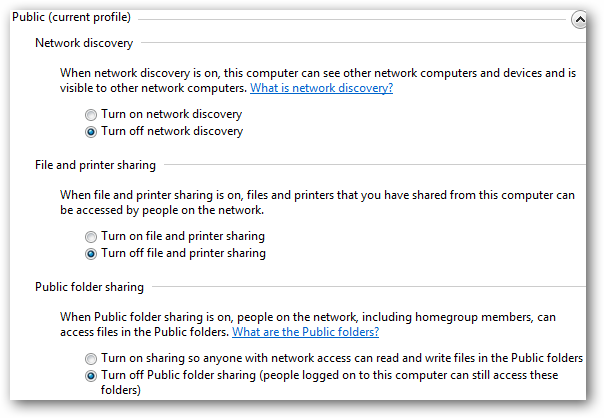
It’s almost vacation time again! That awesome time of year when a lot of us like to travel. Whether it’s off to visit relatives or just heading somewhere where we can relax in a different setting for a bit. Of course that means bringing your laptop and cell phone along. Most hotels, coffee shops, and even restaurants offer the use of free WiFi. The big question is, “How do I keep my info safe out there?” Without getting too into the horrors of what can happen when using public wifi to access and surf the internet, just know that it is a scary movie you definitely don’t want to see. So here are a few pointers to help you stay a little safer while traveling the world this summer. 1. Make sure that your OS, browser, and antivirus are all patched and up to date. Before you head off on your adventure, be sure to make sure your computer is ready to go with you. 2. Turn off sharing. For Windows Vista and 7 use the following to turn off public sharing:
3. Turn on your laptops personal firewall. Windows Firewall is always on by default, so if you’ve turned it off for some reason, it would be a good idea to turn it back on. 4. Use a VPN A VPN, Virtual Privacy Network, is typically a paid service that keeps your web browsing secure and private over public Wi-Fi hotspots. There are a ton of awesome options, so if you need help choosing one, let us know. 5. Use secure websites for sensitive information. The best way to see if the site is secure is to check if it has an “https” address. The “s” stands for “secure socket layer,” meaning the site is encrypted. Another thing to look for is the “green” padlock on your browsers address bar. 6. Consider using a secure browser. There are actually several very good and reliable browsers out in the data stream that can give you automatic encryption. If it is needed. For more info on the latest and greatest, give us a buzz. 7. Read the “Terms and Conditions” of using the free access carefully Some wifi setups are actually placed not by the owner, but by their PR firm, and allow you to use it in exchange for you email address and phone number. To get around this you can use your handy dandy “alternative” email address. 8. Disconnect from the public WiFi when you’re done using it. This is not only courtesy, to keep from using more bandwidth than you need, but it also keeps “sniffers” from getting access. Bonus, this will also help your battery life. 9. Just don’t! You are on vacation! Take some time to do something you wouldn’t do at home. Relax and enjoy sometime away from the virtual world. Tech Force will be here when you get back, and is always ready to help should anything go wrong with your equipment while you’re away! #computerconsulting #computerhelp #computertips The invention of Wi-Fi has been a science fiction dream come true. We can use our laptops anywhere in the house, our phones are using home internet instead of sucking down our cellular data, and our gadgets are all communicating. It’s essentially the backbone of the smart tech boom for home and business alike. Most networks are password-protected with an encryption called “WPA2” and this has been safe and secure, until now.
Recently, a security flaw called KRACK was discovered that allows hackers to break into Wi-Fi networks – even the secured ones. Your laptop, mobile phone, gaming console and even your smart fridge are possibly vulnerable as a result. How KRACK works: The Key Reinstallation AttaCK isn’t a problem with your device or how it was set up. It’s a problem with the Wi-Fi technology itself. The attack gets between your device and the access point (eg router) to reset the encryption key so hackers can view all network traffic in plain text. Since we rely on Wi-Fi so much, this might mean hackers have a front row seat to your credit card numbers, passwords, chat messages, emails, photos and more. NOTE: The hacker must be in physical range of your Wi-fi to exploit this flaw, it doesn’t work remotely like other attacks we’ve seen recently. Given most Wi-Fi ranges extend well past your own home/business, this is small comfort, but important to know. How to protect yourself Run your updates: Software updates are being released which fix the flaw. Microsoft has already released one for Windows, Apple has one coming in a few weeks. Take a few minutes to make sure you’re up to date with all your patches on any device that uses Wi-Fi (your smartphones, laptops, tablets, PCs, game consoles, etc). Unfortunately, some devices may be slow to get an update, or if they’re older, may not get an update to fix this issue at all. If possible, consider using a cabled connection on those older devices or upgrade to one with support. Be very careful with public Wi-Fi: While your local business center, library or school campus has expert IT professionals keeping guard over your security, it’s a very different matter at your local coffee shop. It’s unlikely small locations such as this will be on top of security patches. Remember, a hacker exploiting this flaw only needs to be in the same Wi-Fi area as you, so be careful you don’t give them a dollop of private information with their coffee. Check your browser security: Before sending anything secure over the internet, check you’re using a HTTPS site. You’ll know these by the little padlock you see next to the URL, and the address specifically begins with HTTPS. Major sites like Facebook, Gmail and financial institutions already use HTTPS. If you need help updating your devices, or want us to check if you’re safe, contact us. UH OH! No matter how careful we like to think we are, this can happen to any of us. It only takes a split second to make this catastrophe happen. SPLASH! That mug of coffee, cup of water, or glass of wine is all over your beloved laptop. Here’s what to do if you find yourself in this mess: First, take a deep breath, now is not the time to panic, every second really does count. Next, if your laptop is on, turn it off, unplug it, and remove the power cord. Now, if you can, detach the battery. If your model doesn’t allow for removal of the battery you can skip this step. Then, in a well-ventilated room, tent the laptop over a towel or some absorbent surface, like a microfiber cloth, or stack of paper towels or napkins. This allows any liquid that managed to find its way into your laptop to drain out. Now begin removing all peripherals: mouse dongle, external hard drives, flash drives, if you have an external wireless card take that little fella out too. Basically, if you plugged it in to your laptop, remove it. It is important that you not remove your laptop from this tent position for at least 48, preferably 72 hours. (Warning: Turning a laptop on before it has had a chance to completely dry increases the chances of shorting the components inside. Also, while it might seem a good idea at the time, do not use a blow dryer to try and dry your laptop out faster. This dry heat can severely damage some of the internal components.) Okay, now you can panic… Just kidding. There really is no need. Tech Force has seen this a thousand times, and can get you set straight in no time at all. If you’ve spilled something on your laptop, follow these simple steps, then give us a call. #techforce #computerrepairracinewi #computer #repair #localbusiness #smallbusiness #it #techsupport #laptoprepairracinewi #computerhelpracinewi #racinewi Sometimes computers do wacky things that ring alarm bells and make us dive for cover. Next thing you know, you’re running scans on repeat and demanding everyone come clean about their browsing habits. Fortunately, not all weird occurrences are caused by viruses – sometimes your computer is simply overloaded, overheating or in desperate need of a reboot. Here are the tell-tale signs of a malware attack: 1. Bizarre error messages Look for messages popping up from nowhere that make no sense, are poorly worded or plain gibberish – especially if they’re about a program you don’t even have. Take note of anti-virus warnings too, check the warning is from YOUR anti-virus software and looks like it should. If a message pops up that isn’t quite right, don’t click. Not even to clear or cancel the message. Close the browser or shut down the computer instead, then run a full scan. 2. Suddenly deactivated anti-virus/malware protection You know the best way to get past the guard? Send him for a coffee break! Certain viruses are programmed to take out the security systems first, leaving you open to infection. If you reboot and your protections aren’t back on the job, you are more than likely under attack. Attempt to start the anti-virus manually and you’ll know for sure. 3. Social media messages you didn’t send Are your friends replying to messages you never wrote? Your login details might have been hacked and your friends are now being tricked into giving up personal information or money. Change your password immediately, and advise your friends of the hack. 4. Web browser acting up Perhaps you’ve noticed your homepage has changed, it’s using an odd search engine or opening/redirecting unwanted sites. If your browser has gone rogue, it’s definitely a virus, usually one intended to steal your personal or financial details. Skip the online banking and email until your scans come up clear and everything is working normally again. 5. Sluggish performance If your computer speed has dropped, boot up takes an eternity and even moving the mouse has become a chore, it’s a sign that something is wrong. But not necessarily a virus. Run your anti-virus scan and if that resolves it, great. If not, your computer likely needs a tune-up or quickie repair. 6. Constant computer activity You’re off the computer but the hard drive is going nuts, the fans are whirring, and the network lights are flashing like a disco? It’s almost like someone IS using the computer! Viruses and malware attacks use your computer resources, sometimes even more than you do. Take note of what’s normal, and what’s not. There has been a ton of talk about the cloud. Cloud this, cloud that. But what actually IS the cloud? It’s okay if you don’t know, most people don’t understand it and even some tech people tend to wave their hands towards the sky when trying to explain it!
Since it actually has nothing to do with the white fluffy things in the sky, let’s lay it all out: Cloud computing is about storing and retrieving your data (personal or business) within your own piece of the internet. It’s so you can access it from anywhere, just like you do a web page, and it won’t matter if your office is closed and you’re squeezing in a little work on your phone at midnight. Everything will be saved and ready to pick up when you get back to your desk. Colleagues in different locations can even collaborate on documents in real time. If that all sounds a bit futuristic, think about how an email service like Gmail works. None of your emails are actually being stored on your hard drive or device, they’re stored on the Gmail server and you can access them anytime you like. Your read/send/receive changes are applied instantly, remembered for next time you log in. This is a form of cloud computing. So is Netflix, where you can stream movies and TV shows on demand. All the video is actually stored on a computer somewhere else in the world and sent to your device in tiny pieces as you watch it. Netflix remembers what you watched, where you got up to, and even if you’re hopping immediately from one device to another, it still has it all ready to go. Where is ‘cloud’ data stored? Good question. And it’s why the term ‘cloud’ causes so much confusion. The data absolutely must be physically stored somewhere. Companies who offer cloud storage have huge warehouses dedicated to holding servers whose sole job is to send and receive data all day. And by huge, we mean HUGE. You could get lost walking the rows of servers, just box after box for what seems like forever. The biggest server farms or ‘cloud campuses’ are still growing, but to give you an idea: they can be upwards of 1million square feet. It’s big business, literally. In terms of location, the US and UK are popular server farm locations, but the company could also have copies of your data stored elsewhere in the world. This is so they can fulfill their redundancy guarantees – if disaster hits one location, the other still has a copy. Having additional locations and copies also increases the speed of access. With some companies, you can choose your preferred location so that data doesn’t have to travel quite as far across the world, increasing speed even further, which of course, saves time and money. Collaboration, security, redundancy, AND savings? We’d call that a win. Ready to take advantage of cloud computing? Give us a call at 262-515-9499. With the crazy weather we’re seeing, natural disasters on the rise and cyber terrorism echoing for years, it’s not a case of ‘if’ a disaster will strike your business, but ‘when’. Surprisingly, it’s not the scope and scale of the event that influences how deeply your business is impacted, it’s your business continuity plan.
Put simply, this is the all-important set of precautions and pre-planned responses to an event, laid out in bullet-proof detail and implemented with one driving focus: keeping your business running with little or no downtime. Think about what would happen if your business was hit by a natural disaster tomorrow. Would it survive? How much downtime would it take to push you into dangerous territory? According to an IBM study of all the companies that had a major loss of data, 43% never reopen, 51% close within two years and just 6% will survive long-term. For a fraction of those survivors, business even continued as usual thanks to their ‘failsafe’ business continuity plan. It’s more than disaster recovery, it’s full preparedness that bypasses the need for 2+ weeks of downtime, financial ruin, wasted salaries and reputation loss – but it does require a higher level of planning…in advance. Recommendations to put you in the surviving 6% Prioritize: You’ll need to plan exactly what you’ll recover first and know who’s in charge of making it happen. It goes beyond jotting down a checklist of things to do, it’s taking an analytical, process-based approach to recovery for each unique business perspective. But it’s also realistic: there’s no point dedicating precious time to reviving the email system if your customer data is leaking onto the internet, even if email did rank as your top communication priority! Backup: Of course, the most critical part of your business continuity is having full backups in three places. Why three? One copy locally which you use each day, a backup on another (disconnected) device in the same location, and one in the cloud. That local backup is your life-saver for system crashes, cyber-attacks and the like; the cloud backup comes into play when your business has taken a major physical hit, perhaps from fire or flood. Some businesses can run entirely location-independent when using cloud systems like Office365, which can be enough to put them in that 6% of disaster survivors. Test: Make sure all employees know what the plan is if something goes wrong, and their specific roles in these scenarios. You can test, prepare and rehearse your continuity plan under simulated disaster conditions, which will uncover new obstacles, priorities and additional threats. As your IT environment becomes more complex, carrying more responsibility and risk, so does the importance of a robust business continuity plan. The best BC plans look beyond disaster recovery, taking into account scalability of your system and scope of your individual business, to create strong battle lines that will keep your business operational, both now and for the long term. Credit reporting company Equifax has just revealed that its databases were hacked in a large-scale breach affecting millions across the US, UK & Canada. While no hacking event is ever good news, some are easier to ignore than others – this isn’t one of them. The sensitive nature of the exposed data now requires immediate action for all those even possibly affected.
The short version: Equifax is one of the three main organizations in the US that manages & calculates credit scores. To do that effectively, they have access to almost every piece of financial data for adults in the country, plus pretty much anyone who’s lived/worked in the US. We’re talking social security, tax file numbers, drivers’ license, credit card numbers…the big stuff. On July 29, Equifax disclosed the breach, stating that hackers had repeatedly gotten in through a vulnerability in the web application from mid-May to July of this year. If you’re an Equifax customer: As scary as all that sounds, what’s done is done. Equifax, cyber-security experts & law enforcement officials are on the case, working to minimize the long-term damage. The best action now is to protect yourself against fallout: 1. Go to: http://www.equifaxsecurity2017.com to see if your data may have been affected. There was some news that this site was delivering random results, but Equifax announced it has been corrected. At this stage, it’s safest to assume everyone with a credit history has been impacted, so unless that link gives a definite ‘no you’re safe’ response, continue with the following recommendations. 2. Claim the Equifax free year of credit monitoring & identity theft insurance (if you’re a US resident). If you’re not eligible, consider sourcing your own. As the hacked data will continue to circulate for some time, also consider extending your credit monitoring for a few more years. 3. Keep a close eye on your finances and accounts. Check for notifications of new credit applications, monitor your statements and bills, and immediately report any suspicious activity or sudden change in billing. 4. Change all your passwords to be strong, unique and long. Any of the stolen data may give hackers a free pass into the rest of your bank accounts, email and personal information. 5. Add two-factor authentication where possible. This is when an account demands a second layer of authentication before allowing access or changes – getting the password correct isn’t enough, the hacker would also need to get the special code sent by SMS. 6. Consider freezing your credit report. This makes it harder for identity thieves to open accounts under your name, as access is completely restricted until you choose to un-freeze. Need help with your passwords? Give us a call at 262-515-9499. There’s no doubt about it, business can be tough! You’re juggling employees, customers, suppliers, stakeholders…the list is endless. You’re also operating in a competitive, high-tech economy that keeps trying to speed ahead without you. It’s no wonder you’re craving ways to get ahead of the competition, cut costs, boost productivity and dreaming of a vacation. Here are 3 tech tips that will make your life easier – and maybe get you closer to that ‘World’s Best Boss’ mug.
Consider a commuting policy With better technology and faster internet connections, remote working isn’t just a possibility now, it’s an expectation. Clearly, not for every job (virtual burgers anyone?), but there are a lot of computer tasks in your business that could be done from home. Even if you offer a split week with 1-2 days at home and the remainder in the office, this can be a huge boost to your productivity. From your perspective, remote employees can be more efficient without the distractions of yet another birthday sing-along, they have fewer absences and stay in the job longer. From the employee perspective, they don’t need to waste time commuting, get their work done faster, and generally feel happier and healthier. Don’t cheap out on technology Unsurprisingly, a tech newsletter is advising you to invest in tech, but hear us out. Technology is rapidly becoming the backbone of most businesses, yet we still see people who try and get by with the bare minimum investment and maintenance. And by ‘see people’, we mean they’re our most frequent repair and data recovery clients. When you take shortcuts with your tech you’ll always get higher failure rates, more downtime, and employees who can’t do their job even though you’re still paying them by the hour. When businesses keep old tech longer than they should, thinking of the immediate cost saving, they usually end up paying more in the long term. Embrace the cloud Many of your existing software packages have a cloud version, which would allow multiple people to access it at once and give added backup or synchronization benefits. Your remote workers, mobile staff, accountant or CFO can all view the same reports without anyone having the trouble of sending out separate copies. Cloud technology is also perfect for note-taking and collaboration using software like Evernote or ShareSync. You and your employees can think of ideas while out and about, make a few notes on a mobile device, and have it all synced perfectly to your desktop when you need it. You can even scan in paperwork and have your entire filing cabinet in your pocket. Your business tech can unlock multiple possibilities that will make your days run smoother, more profitable and put you miles ahead of the competition. Ready? Give us a call at 262-515-9499 to make your tech work harder for you. |
Tech Force BlogWe provide you with important, practical tips and insight for your technology and networks for both home and business. Archives
March 2024
Categories
All
|
Get in touch with us! |
See what our clients have to say...
Very pleased with Tech Force! We've been using Tech Force for over four years now. We've had a lot of different people do computer and IT stuff for us, but Tech Force is the first to come in and implement a plan. The plan was executed and we've had no problems. |
More Client Reviews
Read Our Customer Reviews |
We service Racine, Mount Pleasant, Sturtevant, Wind Point, Union Grove, Elmwood Park, Franksville, Caledonia, Kenosha, Somers, Pleasant Prairie, Bristol, Parkside, Oak Creek and Franklin, WI and surrounding areas. Copyright © 2009-2024 Tech Force Computer Service, LLC.






 RSS Feed
RSS Feed
