|
Most technology you buy in stores comes with a warranty of some sort. It might be included or an add-on. Still, it is unlikely to last the lifetime of the device or software, and it seems inevitable that your desktop will die immediately after the warranty runs out. Don’t worry, you still have options. Murphy’s Law of warranty says that you will have no problems with your computer or printer while it’s covered. Then, as if waiting for the most inconvenient time to go bust, the technology fails just after your warranty ends.
After the frustration of looking up that warranty plan to see the expiration date a few weeks ago, your first response might be to take that device back to the store. You’ve noticed they have a service desk, and that’s where you made the purchase. But the technicians on-site are likely to send your laptop to the manufacturer repair. That could be far away, which negates the convenience of taking it down to your local store. You could wait weeks for your item to get to the repair center. Then, it stills needs attention and returning to your store. Also know that many manufacturers charge a premium for outside-of-warranty repairs. Now that you’re one or two years into a relationship with the products, they hope you’ll decide upgrading is easier. They actually have a planned lifecycle for computer hardware and plan the warranty end accordingly. Of course, if you are within days of your warranty's end, ask if the manufacturer will continue to cover the technology. Sometimes it actually will. The manufacturer may also use this opportunity to sell you an extended warranty. Some help with manufacturer warrantyOur first piece of advice? Be proactive about technology issues. Don’t put off getting something looked at. You may discover you could have saved money by having it checked out under warranty. Check your eligibility by visiting the manufacturer’s website and typing in the product serial number to check the warranty. Quickly find the page by searching the manufacturer’s name and “check warranty status.” It’s a good idea to keep track of when your warranty is set to expire. That way, you’ll be more likely to request service in a timely manner. Don’t believe us? Have you ever planned to take an item back to the store only to leave it until the return window has closed? Small business computer repair shops specialize in repairing out-of-warranty devices. We can run diagnostic tests to determine the problem. Then, we'll help you decide whether it’s worth the cost of repairs. If so, we can fix it at a competitive rate. Plus, you get personalized service. There’s also the peace of mind that comes from knowing where your computer is at all times. You're not worrying about it shipping around the country to a manufacturer’s repair shop. The timeline reduces, too, as the IT experts are on-site at a convenient computer repair outfit. We can help keep your computers and other tech devices up and running. Contact us today at 262-515-9499! A single click can be the difference between maintaining data security and suffering massive financial losses. From the moment just one employee takes the bait in a phishing email, your business is vulnerable to data breaches and extensive downtime. Quickly spot the red flags and put phishing emails where they belong: 1. Poor spelling and grammar
While occasional typos happen to even the best of us, an email filled with errors is a clear warning sign. Most companies push their campaigns through multiple review stages where errors are blitzed and language is refined. Unlikely errors throughout the entire message indicate that the same level of care was not taken, and therefore the message is likely fraudulent. 2. An offer too good to be true Free items or a lottery win sure sound great, but when the offer comes out of nowhere and with no catch? There’s definitely cause for concern. Take care not to get carried away and click without investigating deeper. 3. Random sender who knows too much Phishing has advanced in recent years to include ‘spear phishing’, which is an email or offer designed especially for your business. Culprits take details from your public channels, such as a recent function or award, and then use it against you. The only clues? The sender is unknown – they weren’t at the event or involved in any way. Take a moment to see if their story checks out. 4. The URL or email address is not quite right One of the most effective techniques used in phishing emails is to use domains which sound almost right. For example, [microsoft.info.com] or [pay-pal.com] Hover over the link with your mouse and review where it will take you. If it doesn’t look right, or is completely different from the link text, send that email to the bin. 5. It asks for personal, financial or business details Alarm bells should ring when a message contains a request for personal, business or financial information. If you believe there may be a genuine issue, you can initiate a check using established, trusted channels. While education is the best way to ensure phishing emails are unsuccessful, a robust spam filter and solid anti-virus system provide peace of mind that your business has the best protection available. Give us a call to discuss how we can secure your system against costly phishing attacks. 262-515-9499 We often tend to be creatures of habit, particularly when it comes to technology. Passwords are a prime example. Many of us use the same logins for multiple websites and applications because we don't have a photographic memory. A large percentage of users aren’t aware that this is one of the most significant security dangers they can face online. It has a simple fix too. Regularly, in the news today, there are stories about major companies being hacked, their customer data stolen, and their customers left stranded. Hackers commonly use data stolen from one site to access others where login credentials have been reused between accounts. In some cases, access to bank accounts has been gained simply by using a compromised email account.
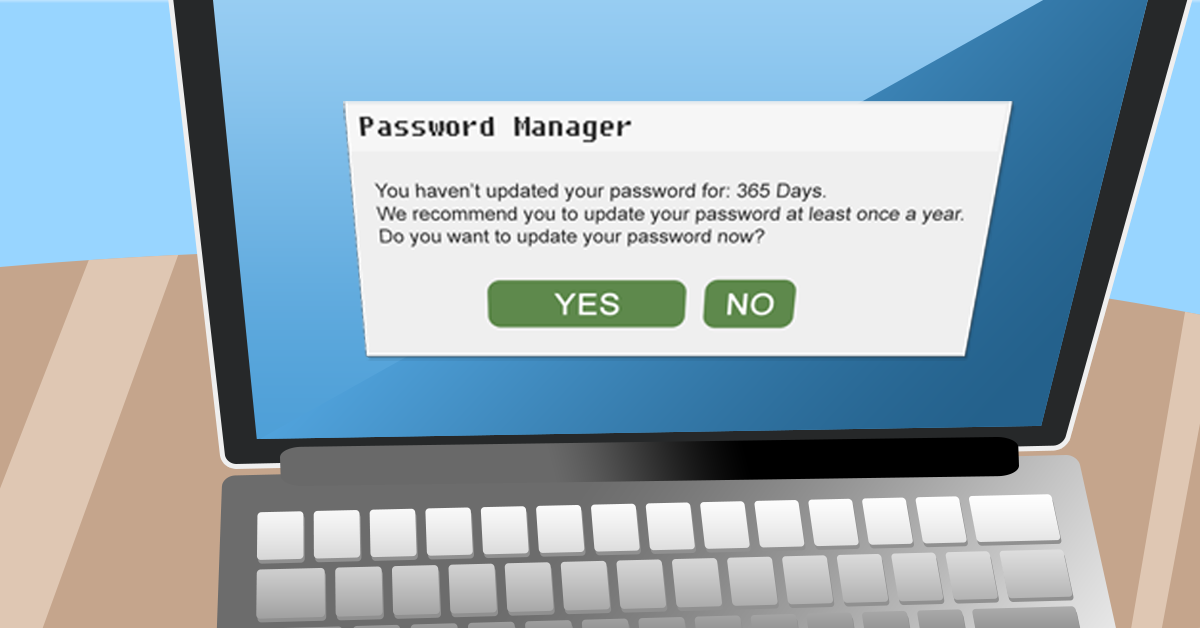
Businesses and individuals can face significant losses simply because a third party outside their control has been hacked or compromised. The Danger Of Old Passwords MySpace is a key example of why old and possibly forgotten services pose a security danger when passwords haven't been regularly changed. Once a thriving popular network, the use of MySpace services declined drastically from 2007 onwards. While many people moved to new social networks, old accounts typically remained abandoned on their servers. Hundreds of millions of accounts remained on MySpace servers many years past the firm's peak. In 2016, MySpace suffered a data leak which exposed usernames, emails, and passwords of 360 million user accounts. Shortly after the hack, these details were published online for anyone to see. Many were used to access email accounts, servers, and accounts that shared the same details. Shared Responsibility Even if you have never had a MySpace or social media account personally, how many of your employees or coworkers have one or more? Many have had more social media, forum, or game accounts than they care to remember. Have their passwords been updated since 2016? Your business network protects your systems, work, and intellectual property. For many firms it's the single most critical component, the backbone to business operations. Keeping it secure regardless of the number of people, staff or clients using it is a crucial task. Consider how many people currently have access and how many of those may reuse their password on another website or service. Just reusing your password once can expose you to the hacking of a third party entirely out of your control. Password Management Good security practice is to use a unique and strong password for every login you use. A strong password should include, where possible, capital letters, lowercase letters, numbers, and character symbols. Many consider this impractical or even impossible, but it is entirely achievable for every firm. It is clearly impossible to manually remember a strong password for each one of the dozens of logins needed today. Few would even attempt to. A password manager makes storing, retrieving, and using unique passwords easy. When using a password manager, an individual is required to remember only one single strong password to access a database which contains a different login password for each service. This database can be synced between multiple devices, saved and backed up to the cloud, and even used to create strong passwords for you. Strong Protection Password managers can be used to implement security policies that demand zero password reuse, between services or over time, and set strict limits over the duration a password can last. With the right policies in place, both your business and your employees are protected against attacks from hackers that have compromised third-party sites. The maximum recommended lifetime of a password for any service is a single year. There's no time like National Password Day to refresh your passwords and start new. To help keep on top of your security and make sure your accounts are safe, give us a call at 262-515-9499 |
Tech Force BlogWe provide you with important, practical tips and insight for your technology and networks for both home and business. Archives
March 2024
Categories
All
|
Get in touch with us! |
See what our clients have to say...
Very pleased with Tech Force! We've been using Tech Force for over four years now. We've had a lot of different people do computer and IT stuff for us, but Tech Force is the first to come in and implement a plan. The plan was executed and we've had no problems. |
More Client Reviews
Read Our Customer Reviews |
We service Racine, Mount Pleasant, Sturtevant, Wind Point, Union Grove, Elmwood Park, Franksville, Caledonia, Kenosha, Somers, Pleasant Prairie, Bristol, Parkside, Oak Creek and Franklin, WI and surrounding areas. Copyright © 2009-2024 Tech Force Computer Service, LLC.



 RSS Feed
RSS Feed
